Ethical Hacking Roadmap and its Advantages for Your Organization
In today’s spirited digital landscape, the looming threat of an ethical hacking roadmap poses a significant challenge for organizations. Ethical hacking, a proactive approach involving skilled individuals specializing in uncovering security probabilities emerges as a crucial solution.
The cybersecurity landscape is progressing, making necessary adaptive measures to shield against potential risks. While traditional security protocols remain fundamental, gaining insights from individuals who comprehend the mindset of potential threats becomes imperative.
Ethical hackers, also known as white hat hackers, play a vital role by delving into systems with straightforward consent from partners Their task is to pinpoint weaknesses and propose enhancements to secure security measures, creating a holistic and comprehensive security approach.
Do You Really Need Ethical Hackers?
Engaging ethical hackers becomes essential as conventional security systems prove inadequate against the expanding array of threats. The proliferation of smart and interconnected devices leaves systems perpetually vulnerable. Hacking, viewed as a financially lucrative pursuit, poses a constant risk to organizations.
As aptly stated by Bruce Schneier, safeguarding hardware is straightforward, but protecting information is intricate, given its ability to transcend geographical boundaries and be pilfered surreptitiously. Without a substantial budget, relying solely on the internal IT department may prove insufficient, potentially leaving vulnerabilities unaddressed and valuable information exposed.
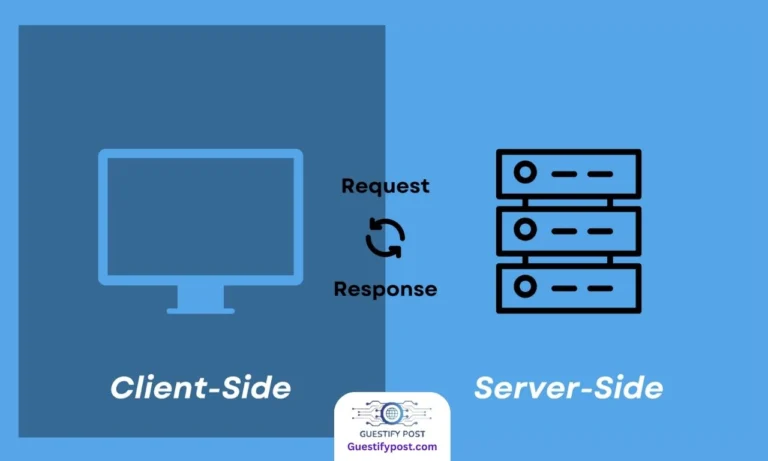
Understanding Hackers’ Methods in Ethical Hacking Roadmap
Effectively preventing hacking requires an understanding of hackers’ thought processes. Traditional security roles may fall short of comprehending the unique methods employed by hackers. This underscores the importance of ethical hackers who, with a perspective akin to malicious hackers, can identify and address security loopholes through penetrative testing.
Penetrative Testing
Penetrative testing, or pen testing, serves as a crucial method to unearth system vulnerabilities. Various approaches, such as targeted testing involving collaboration between organizational staff and hackers, external testing scrutinizing externally exposed systems, internal testing uncovering internal vulnerabilities, and blind testing simulating real attacks, contribute to a comprehensive evaluation.
Ethical hackers, armed with limited information, conduct reconnaissance to simulate real-world scenarios, making pen testing a robust case for augmenting IT security.
Identifying Vulnerabilities of Ethical Hacking Roadmap
Recognizing that no system is entirely immune to attacks, organizations must adopt multidimensional protection. Ethical hackers bring a unique dimension to system security by identifying vulnerabilities that may go unnoticed.
A case study involving a manufacturing organization highlights how ethical hackers provided recommendations for system security improvements, including incident response systems, comprehensive vulnerability management programs, and enhanced hardening guidelines.
Preparedness for Attacks
Acknowledging the probability of cyberattacks, organizations must categorize preparedness. Ethical hackers play an important role in identifying sensitivity before malicious actors exploit them.
The U.S. Department of Homeland Security represents this approach through the Hack DHS Act, which empowers ethical hackers to assess and fortify the security of its complex systems. This collective effort ensures a higher level of preparedness against potential threats.
Conclusion
In conclusion, the synergy between ethical hacking and conventional IT security is imperative for safeguarding enterprise systems. Organizations should define a clear strategy for ethical hacking, drawing inspiration from policies like the Hack DHS Act.
Delineating the role and scope of ethical hackers, establishing checks and balances. It provides legal assurances and contributes to a successful collaboration that enhances system security preparedness. Ethical hacking, when integrated effectively, becomes a valuable asset in the ongoing battle against evolving cyber threats.