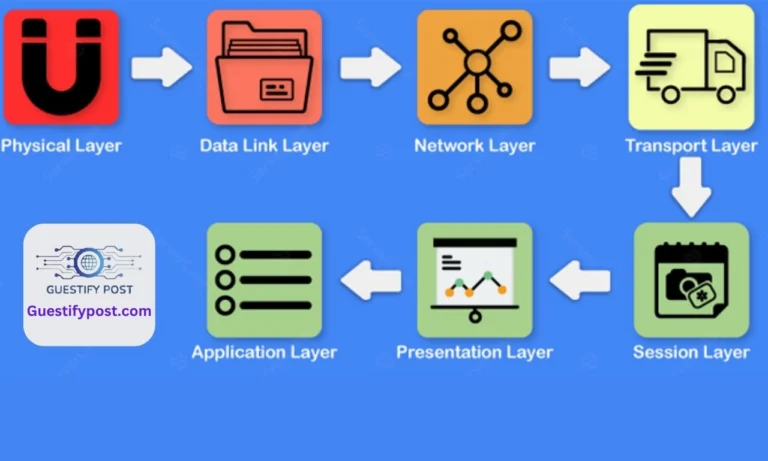
Internet Relay Chat (IRC) The Hidden Charm of User Support
Internet Relay Chat is a world filled to the top with social media giants like Facebook and Twitter, there exists a quiet hero often overlooked – the Internet Relay Chat (IRC). This article seeks to reveal the fresh potential of IRC, serving as a valuable haven for free support, especially within the realm of open-source…